Introduction to Chain-Key Cryptography
In the world of cryptography, ensuring the security and integrity of data is of utmost importance for ICP’s continued operation. One emerging field that is gaining significant attention is chain-key cryptography. This revolutionary approach combines the power of decentralized operation with the scalability of threshold cryptography, resulting in a robust and efficient cryptographic system. We are going to explore the intricacies of chain-key cryptography and how it can revolutionize data security.
🌟 Your Secret Careerist Invite! 🚀
Table of Contents
Understanding the Concept of Decentralized Operation
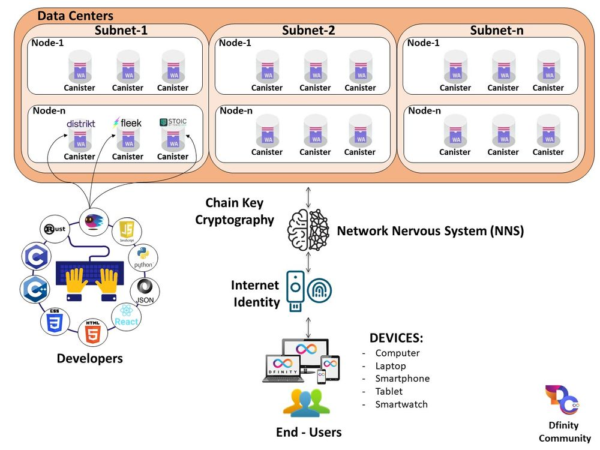
Decentralized operation is a fundamental aspect of chain-key cryptography. Unlike traditional cryptographic systems that rely on a central authority to manage and distribute keys, chain-key cryptography operates in a decentralized manner. This means that the responsibility of key management is distributed among multiple nodes in a network, eliminating the need for a single point of failure.
One of the key benefits of decentralized operations is enhanced security. With no single point of failure, it becomes significantly more difficult for malicious actors to compromise the cryptographic system. Additionally, decentralized operation also ensures that the system remains resilient to attacks, as even if some nodes are compromised, the overall security of the system remains intact.
💼 Show your crypto flair! 💫 Dive in here 👇 for our special merchandise 🎉
Exploring the Scalability of ICP with Threshold Cryptography
Scalability is another crucial aspect of chain-key cryptography, and this is where the concept of threshold cryptography comes into play. Threshold cryptography allows for the distribution of cryptographic operations across multiple nodes, thereby increasing the system’s capacity to handle a larger number of transactions.
The Internet Computer Protocol (ICP) is a prime example of a blockchain platform that leverages the scalability of threshold cryptography. By distributing the computational workload across multiple nodes, ICP can achieve high throughput and low latency, making it suitable for a wide range of applications. Whether it’s processing financial transactions or executing smart contracts, ICP’s scalability ensures that the system can handle the demands of a growing user base.
Benefits of Using Chain-Key Cryptography
Chain-key cryptography offers numerous benefits over traditional cryptographic methods. Firstly, its decentralized nature ensures that the cryptographic system remains resilient to attacks, making it highly secure. Additionally, threshold cryptography’s scalability enables higher throughput and lower latency, allowing for effective processing of large volumes of data.
Chain-key cryptography also offers enhanced privacy. With decentralized key management, users have greater control over their cryptographic keys, reducing the risk of unauthorized access to sensitive information. This makes chain-key cryptography particularly suitable for applications that require stringent privacy measures, such as healthcare or financial systems.
Elevate Your Tech Career! 🚀
Real-World Applications of Chain-Key Cryptography
The potential applications of chain-key cryptography are vast and diverse. One notable use case is in the field of supply chain management. By utilizing decentralized operations and threshold cryptography, chain-key cryptography can ensure the security and integrity of supply chain data. This can help prevent counterfeiting, improve traceability, and enhance overall transparency in supply chain processes.
Another promising application is in the realm of identity management. With chain-key cryptography, individuals can have full control over their digital identities, ensuring privacy and security. This can have far-reaching implications in various sectors, such as banking, e-commerce, and government services, where identity verification plays a crucial role.
Challenges in Implementing Chain-Key Cryptography
While chain-key cryptography offers numerous advantages, it is not without its challenges. One of the primary hurdles is the complexity of implementation. Unlike traditional cryptographic methods, chain-key cryptography requires a decentralized infrastructure and specialized protocols. This can pose difficulties in terms of deployment and maintenance, especially for organizations that are new to the technology.
Another challenge is the interoperability of chain-key cryptography with existing systems. Integrating chain-key cryptography into legacy systems can be a complex task, requiring careful planning and coordination. Additionally, ensuring compatibility with other cryptographic methods and standards can also be a challenge, as different systems may have varying requirements.
🔥 BOOST YOUR QA CAREER! Embark on a transformative learning experience in QA Automation Engineering, starting from ground zero. Gain the skills needed to secure a job within a year, or get your money back.
How to Implement Chain-Key Cryptography in Your Organization
Implementing chain-key cryptography in your organization requires a strategic approach. Firstly, it is essential to assess the specific needs and requirements of your organization. This includes evaluating the level of security, scalability, and privacy that your organization requires.
Once the requirements are identified, the next step is to design a decentralized infrastructure that can support chain-key cryptography. This involves setting up a network of nodes that will be responsible for key management and cryptographic operations. Additionally, specialized protocols and algorithms may need to be developed or adopted to ensure the seamless integration of chain-key cryptography.
💼 Master Sales Engineering essentials! 🛠️ these concise courses cover it all. Elevate your career with practical knowledge and hands-on experience
Comparison of Chain-Key Cryptography with Other Cryptographic Methods
Chain-key cryptography stands out from traditional cryptographic methods in several ways. Its decentralized operation provides enhanced security and resilience. Traditional methods, such as public-key cryptography, rely on a central authority, which can be a single point of failure. Chain-key cryptography eliminates this vulnerability by distributing key management across multiple nodes.
In terms of scalability, chain-key cryptography offers significant advantages over traditional methods. Threshold cryptography allows for increased throughput and lower latency, enabling the efficient processing of large volumes of data. This scalability is particularly crucial in today’s data-driven world, where organizations deal with ever-increasing amounts of information.

Future Prospects of Chain-Key Cryptography
The future of chain-key cryptography looks promising. As organizations continue to recognize the importance of data security and privacy, the demand for robust cryptographic solutions will only grow. Chain-key cryptography offers a unique combination of decentralized operation and scalability, making it well-suited for the challenges of the digital age.
💼 Elevate your QA game with these Automation Courses! 🚀 Master scripting, testing frameworks, and more. Take the next step in your career journey now!
Keep in mind that advancements in technology and the increasing adoption of blockchain platforms like ICP will further fuel the development of chain-key cryptography. As the field continues to evolve, we can expect more efficient and user-friendly implementations of chain-key cryptography, making it accessible to a wider range of organizations and applications.
💼 Show your crypto flair! 💫 Dive in here 👇 for our special merchandise 🎉
Final Thought
Chain-key cryptography represents a significant advancement in the field of data security. By combining the benefits of decentralized operation with the scalability of threshold cryptography, chain-key cryptography offers enhanced security, improved scalability, and greater privacy. While there are challenges in implementing and integrating chain-key cryptography, the potential applications and future prospects make it a compelling choice for organizations seeking robust cryptographic solutions. Investing in chain-key cryptography can help organizations stay ahead in the ever-evolving landscape of data security and privacy.




