This article will examine how cryptocurrencies operate. From the creation of safeguards designed to protect investors, like smart contracts’, to ‘consensus algorithms’ and their transactions, let’s examine the structure of this cryptic financial innovation known as crypto.
Table of Contents
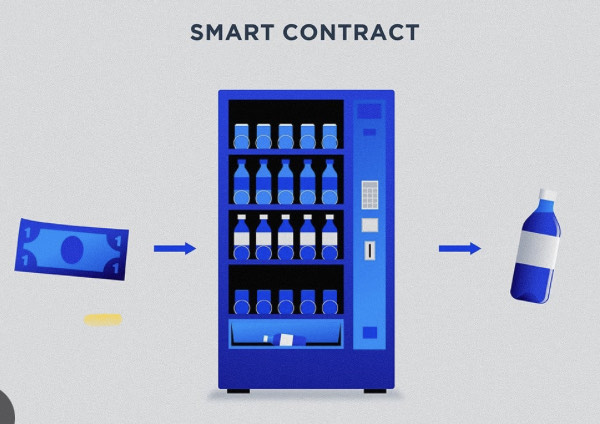
Smart Contracts
You may have heard that cryptocurrency is a programmable currency. However, what does this entail, and how is it accomplished?
A blockchain network executes smart contracts, which are essentially pieces of code, to carry out a predetermined set of tasks. Once deployed, the code of a smart contract cannot be altered and can be automatically executed or enforced without the involvement of a third party.
Why are smart contracts necessary?
Multiple computers collaborate and concur to keep the distributed ledgers of cryptocurrencies in sync. At their foundation, cryptocurrencies enable the transfer of ownership of units of the currency from one party to another; this transfer is recorded in the ledger for all time. But what if you want to do more than simply transfer currency units?
What if you only want to transfer these units after a certain amount of time has passed or if a certain event has occurred? Smart contracts are here!
Smart contracts utilize the immutability property of blockchains and are irreversible.
How and where are smart contracts produced and deployed?
Depending on the smart contract platform for which they’re intended, smart contracts can be written in a variety of programming languages.
Today, a multitude of smart contract platforms exist. The list is lengthy, but the most well-known are Ethereum, NEO, EOS, Cardano, Stellar, and VeChain. On Ethereum and many other platforms, smart contracts are written in a language called Solidity, which was designed particularly for smart contracts. On other platforms, however, such as NEO, smart contracts can be written in generic programming languages such as C#, Java, and Python.
What are use cases of smart contracts?
While the use-cases for smart contracts are limited only by the author’s imagination, token creation is the most common use-case for smart contracts. The majority of crypto tokens are merely smart contracts operating on a smart contract platform. In fact, this use case is so prevalent that most, if not all, smart contract platforms have standards for creating tokens. On Ethereum, this standard is known as ERC-20, while on NEO, it is referred to as NEP5. These specifications define the minimum set of capabilities that a smart contract must possess.
The brilliance of public smart contract platforms is that anyone can write, deploy, and execute a smart contract on all the network’s computers. Invoking a smart contract function is not always free due to the fact that running a smart contract requires resources from all the devices in the network. Most smart contract platforms determine the cost of an invoked function based on its complexity. A smart contract cannot be modified after its deployment.
Oracles and smart contracts
Sometimes, smart contracts necessitate input from the real world. Imagine a smart contract that enables individuals to speculate on the outcome of a football game. The smart contract is ideal for administering funds and ensuring that winners receive their winnings and losers receive nothing, but it cannot possibly predict the outcome of the football game. Invoking a function is necessary for one or more third parties to provide the smart contract with the football match’s outcome. This type of third entity is known as an oracle.
A key characteristic of a smart contract is that it verifiably does what it claims it does – nothing more and nothing less – and that its code cannot be modified once it has been deployed. The contract eliminates the need for parties to trust each other because they are aware of what the smart contract does; therefore, everything is imbued with a sense of trust, regardless of relationship or geographic location.
There is a good possibility that smart contracts will facilitate the majority of human transactions in the future. We have only scratched the surface of the use cases for tamper-free, verifiable, programmable interactions via smart contracts in banking, insurance, digital identity management, supply chain, gaming, and wagering.
ERC-20
ERC-20 may sound like a military codename, but it is considerably simpler than that. ERC-20 tokens are simply tokens created on Ethereum, a popular cryptocurrency platform.
Ethereum Request for Comments, or ERC-20, The number “20” is merely the number associated with the initial proposal. ERC-20 signifies the nine requirements that a cryptocurrency must adhere to in order to operate on the Ethereum network.
Ether is the principal currency on the Ethereum network; however, the Ethereum Blockchain supports numerous ERC-20-compliant cryptocurrencies. The network enables users to construct their own cryptocurrency without having to reinvent the wheel.
Functions of ERC-20 tokens
To operate efficiently on the Ethereum network, ERC-20 tokens must include nine functions (six mandatory and three optional). These functions ensure that ERC-20 Tokens can effectively communicate with one another.
The three optional functions are simple. When creating a token, you have the option to assign it a Name, a Ticker Symbol (such as ETH), and an Adjustable Divisibility (how many decimal places the token will support). The remaining six are more technical, so we will bypass them for the time being.
The introduction of the ERC-20 standard enables all Ethereum Network initiatives to interact with one another without the need for individual interaction programming. It guarantees complete flexibility and fluidity among all ERC-20 Tokens.
ERC-20 is not as complex as it may appear. It is essentially a collection of nine functions that enable projects built on the Ethereum Network to interact in a controlled and consistent manner.
The standard also serves as a form of built-in security within the Ethereum Network by enforcing certain constraints that deter fraudulent behavior.
The creation of the ERC-20 Standard is directly responsible for the massive number of Ethereum Network-based initiatives and the ICO boom of 2017. It made it simple for the average user to design and implement their own cryptocurrency initiatives, which is why it remains the most popular token format to this day.
Consensus Algorithms
In our article titled ‘What is Consensus?” we define consensus and explain why a cryptocurrency requires consensus between nodes to validate transactions. Nevertheless, not all cryptocurrencies reach consensus in the same manner; these distinct procedures are known as Consensus Algorithms. A cryptocurrency’s Consensus Algorithm is an integral element of its design.
It determines how many nodes a network can support, how vulnerable it is to attack, and how quickly transactions can be confirmed. For these reasons, it is essential to select a consensus algorithm capable of achieving the optimal level of decentralization, speed, and security for every use case.
There are numerous algorithms, and more are created every day, but the following are the most prevalent:
Proof of Work
Bitcoin, the oldest and most popular cryptocurrency, employs the proof of work (PoW) consensus algorithm, which was introduced in 1993. In proof of work, miners compete to solve a mathematical problem using faster computers. The first miner to solve the mathematical problem certifies the transactions in the block and is awarded the block reward and transaction fees.
As the network’s total processing power increases, the math problems become more complicated, preventing them from being solved quicker. In this consensus algorithm, a 51% attack is only possible with 51% of the network’s total computing capacity, which is why Bitcoin is so difficult to attack at the present time.
Proof of Stake
Peercoin introduced proof of stake, or PoS, as a consensus algorithm for the first time in 2012. It is viewed as a potential solution to the substantial quantity of electricity that proof of work consumes. As with the subsequent systems, it does not require competing computers to confirm transactions. Instead, Proof of Stake uses a weighted random selection to determine which node will confirm the following block and receive the associated block reward.
Delegated Proof of Stake
Delegated proof of stake (DPoS) is a proof of stake variant that minimizes the number of nodes that validate blocks. Users must vote for representatives who will validate bans on their behalf. Similar to a mining pool, block rewards are then distributed among the nodes’ voters. Transaction speeds are significantly faster when there are fewer validating nodes, but some people doubt the extent of decentralization that these platforms can achieve.
EOS is most well-known for employing this algorithm; however, due to its faster transaction speeds, it has rapidly become one of the most popular algorithms besides proof of work. Unfortunately, having a small number of nodes increases the likelihood of collusion, and as the public Lisk cartel demonstrates, this is a very real danger.
Byzantine Fault Tolerance
Practical Byzantine Fault Tolerance (BFT) is a method for achieving consensus if at least two-thirds of the network can be trusted. To validate blocks, the nodes in these cryptocurrencies are preselected and vote in BFT rounds. Typically, this method of consensus is more “scalable, with a high throughput and a swift finality. Unfortunately, because they cannot support a significant number of nodes, they are more centralized. BFT consensus is deterministic, and each round of voting has a fixed number of participants.
Too many PoX protocols exist to introduce them all individually. Our beginner’s guide to consensus mechanisms provides a summary of the most well-known PoX consensuses currently in use.
The Role of Altcoins in the Crypto World
This article has likely taught you that the crypto world is self-policing. It is based on both the freedom to explore and innovate and a mutual, technology-assisted system of checks and balances designed to ensure the system is fair and free of corruption. This financial system could be termed utopian if implemented properly. While crypto is still in its infancy, we are eager to see what the future holds.




